Current Challenges
Today’s complex IT environments have created challenges around identity governance, management and enforcement of access controls within the organizations. Access policy violations can expose organizations to various challenges including audit non-compliance, fraud risks, data leakage /theft, managing stale / expired access across the organization. Access governance (AG) is an aspect of information technology (IT) security management that seeks to reduce the risks associated with end users who have unnecessary access privileges. The need for access governance has grown in significance as organizations seek to comply with regulatory compliance mandates and manage risk in a more a strategic manner.
Why Do We Need It?
In today’s organization, users (employees or contractors) have access to several technology privileges that help them do their job effectively. These privileges (e.g. email ID, distribution lists, application access, access to shared files/folders, specific productivity software, internet, admin rights etc.) are typically linked to their role, position or location. It becomes essential for organizations to map the privileges to these users and ensure each user gets a right set of privilege. To add to the complexity users go through their own lifecycle within the company in terms of their promotions, transfers, temporary assignments and finally the exit. It becomes absolutely essential in this scenario for the privileges to be re-mapped to the new roles and provision them quickly and more importantly de-provision what’s no longer permitted.
AKS Solution
AKS's Access Governance has looked at the gap in the existing solution landscape and build out an innovative approach.iGovern leverages and enhances customer’s existing identity store for identity management- All applications continue to use their existing identity and authentication mechanisms, only linking to
iGovern and Identity store from a mapping perspective is required - All components of endpoint control, infrastructure elements
and shared services are governed through directory services that are already present - Open architecture build on Rest API gives a quick and seamless connectivity to application landscape
iGovern has a complete mechanism to automatically provision/de-provision all technology privileges.iGovern brings the following components to deliver the above objectives
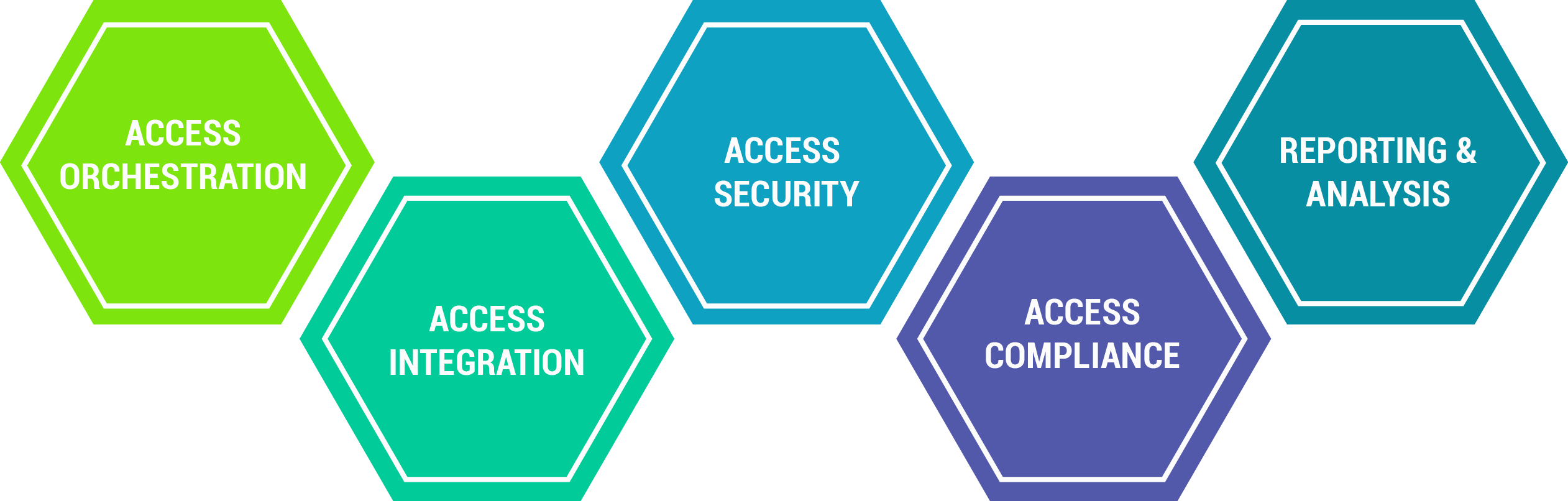
ACCESS ORCHESTRATION
- Ability to orchestrate access any user type Employees, Contractors, Temp workers and across any stage Joiner-Mover-Leaver
- Automated workflow approval process linked automated provisioning and de-provisioning
- Access to any service type – structured or unstructured
- Any access request type –
self services , automated, temporary
ACCESS INTEGRATION
- Integration framework for pulling data from HR/Contractor management systems for identifying user movement
- Ability to integrate with supporting systems eg. Directory Services (MS AD, Open LDAP), ITSM systems (ServiceNow, Remedy)
- Integration with applications using Rest API or custom integration framework
- Access to endpoint control, application, shared services, infrastructure or cloud applications
ACCESS SECURITY
Self service password management, password enforcement and integration with SMS gateway for OTP- Ensures accurate identity data by weeding stale access profiles
- Ensure controlled access based on organizations rules and ability to flag accesses which are granted without due process
ACCESS COMPLIANCE
- Control and automate user access to service types, as well as enforce policy in line with compliance requirement
- Ability drive access recertification process
- Comprehensive compliance reporting capability
REPORTING & ANALYSIS
- Rich reporting framework for regulatory and audit reports
- Access compliance, risk posture, alerts and exceptions
Aks Infotech Solutions Group has over 50 years of expertise in delivering customized information technology solutions across all platforms for midsized to large organizations. Our people want to work with your people. For more information, visit www.aksinfotech.net or contact us at 6093014607 to learn how our proven methodology can help your organization increase productivity, reduce costs and mitigate risks.
Contact Us